SCAMMERS TARGET COLLEGE CAMPUSES WITH PHISHING EMAILS
SCAMS FLOOD STUDENT AND FACULTY INBOXES AS UNIVERSITIES SCRAMBLE TO AVOID DATA BREACHES.

The pop-up said that the computer was compromised, and urged Smiles to call the number on her screen immediately to avoid a data leak of her credit card and google account information. Startled by the sudden warning, Smiles promptly called the number on the screen.
She proceeded to reveal her computer’s serial number, as well as her mother’s credit card information to the scammer. In an attempt to protect her data, Smiles unknowingly handed it over to an eager scammer.By following the instructions on the pop-up notification, Smiles fell victim to the growing number of phishing scams targeting college students across the country.
ANATOMY OF A PHISHING EMAIL
Phishing is a type of online scam in which attackers trick individuals into revealing sensitive information like passwords, credit card numbers and other personal data. Phishing is typically facilitated through fraudulent emails or messages that appear to be from a legitimate source, in order to gain access to sensitive information or infect the victim's device with malware. James Perry, a scamming expert from the National Consumer League, said: “A person could be a victim of a phishing scam by giving up their name, social security number, mailing address, and things like that.”
Click through the email example below to learn Perry’s tell-tale signs of phishing emails.

From
If the sender’s email domain is not from the place it’s claiming to be from (ex: Citi Bank’s email domain may be jsmith109@hack.net). Perry said this is a dead giveaway when it comes to identifying phishing emails. Typically, if a government agency is contacting someone, they would use a “.gov” account instead of a “.com” or “.net” account. “Consumers really need to just look at the return address,” Perry said.
Subject
If there are misspellings in the email and the subject seems unprofessional. Perry said another key to spotting phishing emails is checking an email’s grammar: “Grammar should be good.” If there are typos or if the nature of the email seems off (ex: very casual tone in an email supposedly originating from a professional organization), it is likely that the email is a phishing attempt.
Dear
If the recipient is addressed as “customer,” and not personally mentioned. Phishing scammers often send an email that uses a basic name, such as “customer” or “consumer.” However, if a phishing scammer has your name, they may add it in to make the email seem more legit. “They will run off the person’s personal information,” Perry said.
Please
A sense of urgency (something needs to be done immediately) or asking the recipient to give up excess personal information. Phishing emails often ask for an individual’s sensitive information, like your social security number or mother’s maiden name. They often use urgency to persuade whomever they’re trying to scam to act on impulse. “When it comes to phishing, you have to realize that when you’re online, you just don’t provide certain information,” Perry said.
www
If the link is broken, the website is fake, or the URL doesn’t match the website’s real URL (ex: banking emails should go to the bank’s URL, not a random URL site) or if the site seems phony. Those fake sites will often ask for very personal information, such as someone’s social security number. “Because the consumer feels as though they’re on a legitimate site that they have a relationship with, they don’t have a problem providing that information,” Perry said. Legit sites usually can be checked by simply looking them up on a search engine or checking the actual URL link.
Signature
The concept of phishing is to get somebody to respond to a message that appears legitimate, According to Gene Spafford, a professor of Computer Science at Purdue University. Online scammers seek out personal identifying information and employ a variety of methods to lure people into giving it up.
Many regular phishing scams are approached opportunistically. Joon Park, a professor of information studies at Syracuse University, said many attackers do not have a specific target audience and would rather distribute a large amount of scams across the web.
Data from Cyber Talk, a cyber security news outlet, states that roughly 15 billion scam emails made their way across the internet daily, and about 83% of organizations experienced phishing attacks in 2021.In order to execute high volume phishing efforts, scammers employ different methods to target specific communities.Spear phishing is a common method used to attack university students, teachers, and administrators alike.
Spear phishing allows online scammers to focus on a target audience and individualize personal attacks to secure personal information, according to Park.Security technologist Bruce Schneier claims that the individualized attacks have recently been hitting college campuses, and are an easy way to deceive members of a university. “You get an email saying you’ve got this fellowship here, and I’m here to help you get housing,” Schneier said.
“It’s someone who’s scraping names off some website, and then scamming people to give them money for apartments that don’t exist. That’s kind of university specific.”
GET SCHOOLED ON THE SCAMMING TERMS
Spear Phishing
Spear phishing is a type of targeted phishing attack that is aimed at specific individuals or organizations. Unlike regular phishing attacks, which are typically sent to a large number of random email addresses in the hopes of tricking some of the recipients into divulging sensitive information or clicking on a malicious link, spear phishing is much more personalized. “For instance, if I was going to send something to everybody at Syracuse [University], I might customize my message to have something to do with a local bank or credit union that a lot of people at Syracuse might use,” said Gene Spafford, professor of computer science at Purdue University.Smishing
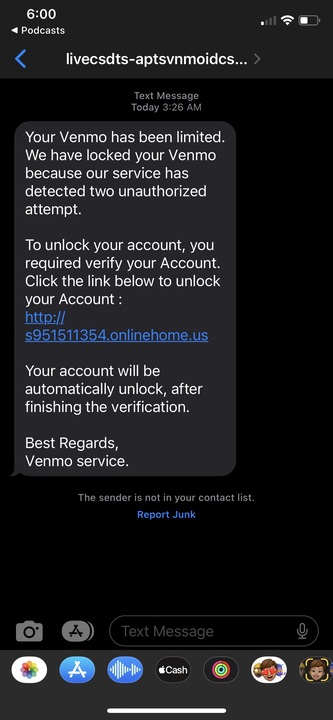
Smishing scams, unlike traditional phishing attacks that rely on email, use text messages as the mode of communication. Like the phishing scam, a smishing scam aims to make the user download malicious code or directs them to a link intending to steal your personal information. The most common type of smishing scams are directed at bank account logins, which try to gain access to a victim’s banking information. “For example, you get a text from some guy saying you have to text the number on the screen, or your Amazon account is frozen because of some problem,” Park said.
Vishing
Phone calls and voicemails are the mode of scamming in vishing. The scammers use a number of techniques to try and convince their target to hand over the desired information such as: using intense technological jargon, mumbling answers, ID spoofing (a technique that changes the caller ID to something more reputable), and AI voice deep fakes enable vishing scams to take on a variety of forms to attempt to obtain personal information over the phone.Whaling
Whaling is the term used to target and harpoon company executives. It aims to gain access to a major part of a company's records, such as login information for an employee, sensitive company information, or even access to a company’s VPN (Virtual Private Network). “A very specific target, usually a high value target, is the only person getting the message and the message that is sent to that person is highly customized,” said Spafford.Pharming
Pharming is a type of online scam that redirects users from legitimate websites to fake, malicious ones. It is often very hard to recognize the techniques scammers are using. As the name suggests, pharming is meant to target swaths of people, even those that would normally be wise to other phishing attacks. Pharming works by rerouting the target from an intended website with links that look real to a malicious one.College students are not only susceptible to these attacks, but university administration as well.
Bruce Strong, a professor of visual communications at Syracuse University found himself led astray by a scam email disguised as a personal email from his colleague. “I got an email from someone that was pretending to be Melissa Chessher, who was the chair of the Magazine News and Digital Journalism department here at Syracuse.
In the email she asked me to run and pick up Google Play gift cards for the office at a local store, which I ended up purchasing,” he said.After buying the gift cards, Strong realized that something was off. He replied to the original email, asking the scammer to confirm that she was Chessher, but never heard back. He came to the conclusion that he was being spoofed, and did not hand over the gift cards.An attack like this, which appeared legitimate at the time, was challenging to identify as fake in the heat of the moment.
Spear phishing scammers reel in victims by creating realistic scenarios specific to the individual. As former Syracuse University student Kaitlin Rowe filtered through her inbox, checking notifications from professors and organizations about deadlines and meetings, one email stood out.After recently being admitted to the University of Vermont graduate school program for physical therapy, Rowe noticed an email that appeared to come from UVM.
Many universities utilize Outlook email accounts to facilitate university communications. The email Rowe received said that she could not have two university outlook accounts at the same time, and she was asked to provide information so she would not lose her saved data from her SU undergraduate account when she created her email for her UVM graduate program. “They sent me a link, and they’re like, to make sure we don’t delete both of your accounts, please click this link and fill out this form,” Rowe said.
“So like an idiot, I clicked the link and I filled out the form.”Similar to Strong’s spear phishing attack, Rowe’s scammer knew of her post-graduation plans and used this personal information to convince her to give over compromising personal information. Phishing is a mainstream incident on college campuses, prompting campus IT professionals to explore solutions.
3 COMMON PHISHING SCAMS
TARGETING CAMPUSES
Phishing is a type of online scam in which attackers trick individuals into revealing sensitive information like passwords, credit card numbers and other personal data. Phishing is typically facilitated through fraudulent emails or messages that appear to be from a legitimate source, in order to gain access to sensitive information or infect the victim's device with malware. James Perry, a scamming expert from the National Consumer League, said: “A person could be a victim of a phishing scam by giving up their name, social security number, mailing address, and things like that.”
Click through the email example below to learn Perry’s tell-tale signs of phishing emails.

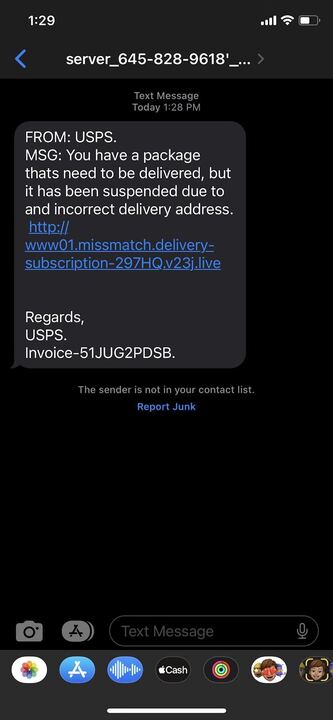
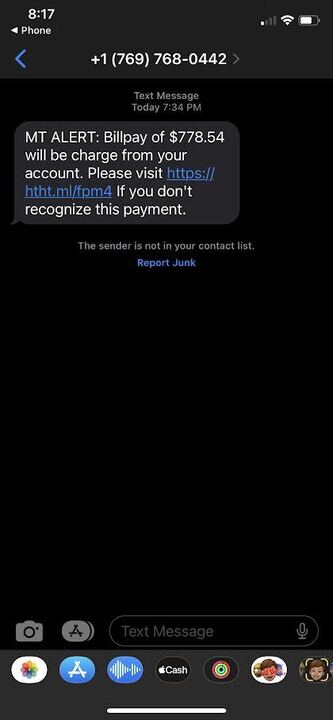
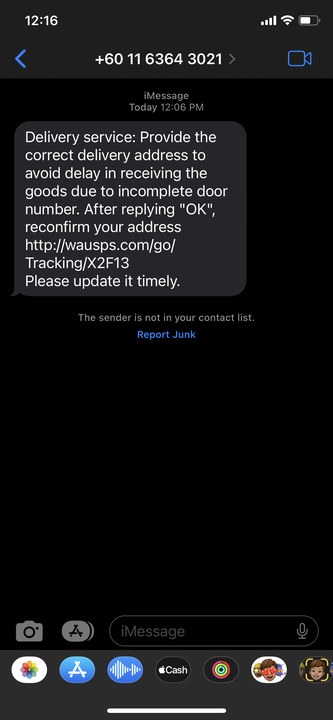
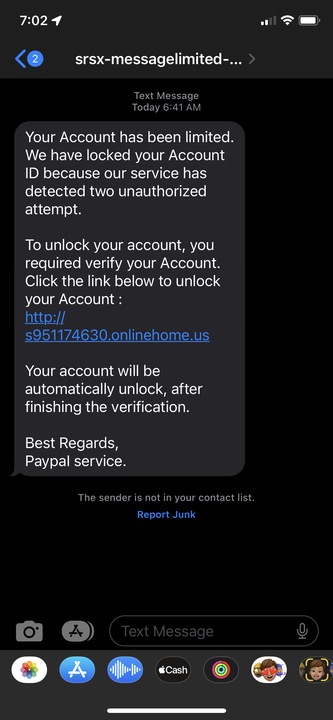
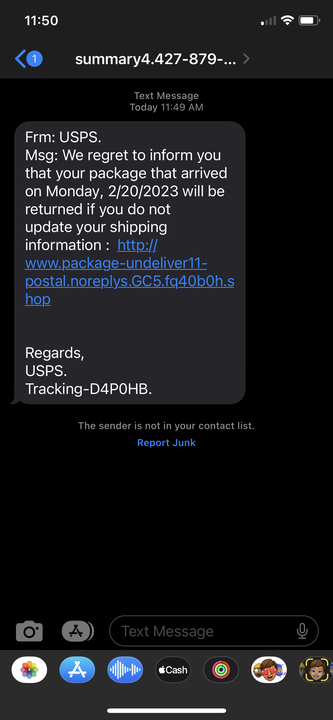
The Local Job Posting

The Account Access Scam

The Housing “Offer”
Christopher Croad, Syracuse University’s Chief Information Technology Officer understands the problem of personalized emails eroding their defense mechanisms and reaching students and administration alike. Although Croad claims most scams are unable to break through the cybersecurity wall, technology is not strong enough to eliminate every single one.
“The problem is, to make email filters get rid of every single bad email, it’s also going to get rid of a lot of good emails, accidentally, and we don’t want that,” Croad said. “We don’t ever want to stop a valid email from coming through. We have to find this balance.”
The struggle of filtering good versus bad emails on college campuses is partially rooted within the legality of the First Amendment of the U.S. Constitution.
Angelos Stavrou, a professor of Electrical and Computer Engineering at Virginia Tech University, said online scammers can use free speech as an advantage to break through the cybersecurity wall. “You have now a lot of people who can potentially abuse the freedom of speech,” Stavrou said.
“We have to let a company who is doing marketing reach out to us, whether we are interested in that product or not. But if we do that, then it opens up the door for spam or phishing because phishing is a legitimate looking email.
”With universities needing “good” emails to reach their respective audiences, the ability for scammers to pose as authentic emails makes it difficult to filter them out.
Many scams present information in an urgent manner, forcing individuals to feel like they need to take immediate action. Bruce Strong believes taking a deep breath and slowing down is an important step when identifying these attacks.
“Even if you’re in a hurry or something urgent pops up, just slow down and check to make sure it's legit,” Strong said. In addition to slowing down, there are many signs one can look for when identifying the legitimacy of a phishing scam.
“First of all, question, is it too good to be true? If the message is too good to be true, it probably is,” Croad said. “Question where it's coming from. Look at the email address and check the source of it. Look at the links. Do the links actually go?
These are all some big red flags to consider.”Experts urge potential victims to learn how to spot signs of a scam before clicking links or revealing personal information, as prevention is easier to address than the ramifications of compromised information.
“It’s like when you’re having an argument with a friend, stop and take a deep breath so you don’t say something mean,” Smiles said. “When presented with a scam, stop and take a deep breath so you don’t offer any personal information.”